TL;DR: The 2000s witnessed the rapid evolution of malware into more aggressive worms that exploited software vulnerabilities to autonomously spread and cause significant disruption. Notable worms such as ILOVEYOU, Slammer, and Conficker leveraged social engineering, multi-vector propagation, and advanced evasion techniques. This era also marked the rise of botnets, large-scale distributed denial of service (DDoS) attacks, and the expansion of malware to mobile devices, laying the groundwork for the sophisticated malware we see today.
The Adolescence of Malware: The Rise of Worms. The 2000s
The turn of the century marked the “adolescence” of malware, a period characterized by the rapid evolution of malicious software into more aggressive and widespread forms, particularly worms. The rise of Internet access, combined with the increasing popularity of operating systems such as Microsoft Windows, provided fertile ground for worm development and propagation. Unlike earlier malware, which often served as proof-of-concept or were created for experimentation, worms in the 2000s had more destructive intentions: they exploited security vulnerabilities, spread autonomously, and caused massive disruptions.
The decade began with the well-known ILOVEYOU worm (2000) [1]. Developed in VBScript, this malware targeted Windows, borrowing ideas from Melissa. When infected, it sent itself to all contacts in the user’s Microsoft Outlook address book. It could also spread through mIRC, a popular Internet Relay Chat client at the time. At a moment when businesses and individuals were undergoing digital transformation, the ILOVEYOU worm caused massive disruption, leading to an estimated $8 to $10 billion in damages worldwide [2, 3]. Figure 1 shows an email with an attachment infected with ILOVEYOU from those days. It demonstrated the effectiveness of exploiting human curiosity and trust through seemingly innocent messages.
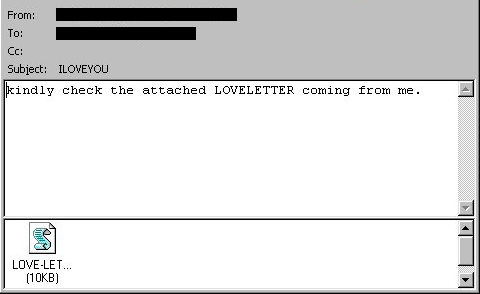
ILOVEYOU (source: Wikipedia)In the same year, the first IRC bot named GTBot also appeared, spreading as a Trojan horse disguised as a software utility. Once launched, it used the mIRC client to communicate with attackers, who leveraged infected systems for DoS attacks. Continuing the trend of VBScript-based worms, the Anna Kournikova worm appeared in 2001. It spread by launching a VBScript program when an email attachment was opened in Microsoft Outlook, forwarding itself to all contacts in the victim’s address book (see Figure 2). Its rapid dissemination led to DoS issues in many email servers worldwide [4]. Interestingly, Anna Kournikova was created using Kalamar’s VBS Worm Generator, a tool specifically designed to generate new worm-like malware of that time.
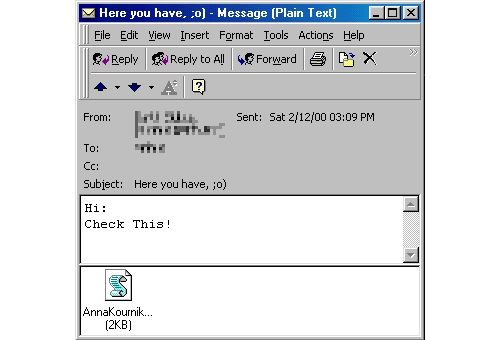
Anna Kournikova (source: Memories of the Anna Kournikova worm, Graham Cluley)The early 2000s also saw the rise of more technically advanced worms, such as Sadmind [5] and CodeRed [6], which targeted vulnerabilities in server software. Specifically, Sadmind infected Solaris and Microsoft IIS servers, defacing websites [7], while CodeRed exploited vulnerabilities in Microsoft IIS to similarly deface web pages [8] (see Figure 3 for an example). The impact of these worms was amplified by their focus on servers, which, when compromised, affected numerous users.
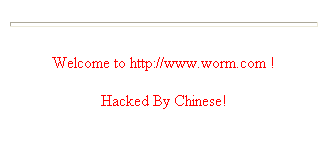
CodeRed worm (source: Wikipedia)Soon after, in 2001, Nimda emerged, notable for its ability to execute without any email attachment being opened. Due to configuration vulnerabilities in Microsoft Internet Explorer, merely previewing an email would activate Nimda [9]. It spread across Microsoft Windows workstations and servers, moving from client to client using email, open network shares, and from web server to client by exploiting backdoors left by Sadmind and CodeRed.
Later in 2001, Klez appeared [10]. Like Nimda, it did not require email attachments to be opened, and it further complicated matters by spoofing the sender’s identity. Some variants of Klez included drive-by-downloads (a drive-by-download attack is the inadvertent download of malicious files or potentially unwanted software onto a computer system), file-infectors, and file deletion behaviors, marking a shift toward more harmful intentions, while others attempted to remove Nimda and CodeRed from infected systems.
MetaPHOR (also known as Win32/Simile or Etap), the first metamorphic virus, was released in early 2002. It was capable of self-transformation, rewriting its own code, and was written in assembly [11]. Around the same time, MyLife appeared as a mass mailing worm, while Tanatos emerged as a Trojan capable of keylogging and backdoor functions, affecting Windows systems [12, 13].
The first recognized spammer worm, Sobig, emerged in 2003, spreading via email and network shares [14]. Another major event in 2003 was the release of Slammer, which further illustrated how quickly malware could spread. Exploiting a buffer overflow vulnerability in Microsoft SQL Server 2000, Slammer managed to infect hundreds of thousands of systems in a matter of minutes, leading to widespread network congestion and denial of service [15]. Its ability to spread so rapidly earned it the nickname of the first “Warhol worm” [16], capable of infecting nearly the entire vulnerable Internet within 15 minutes. Figure 4 shows the UDP package sent by Slammer to compromise MS SQL servers. Spybot, the first peer-to-peer worm, also appeared in 2003 [17].
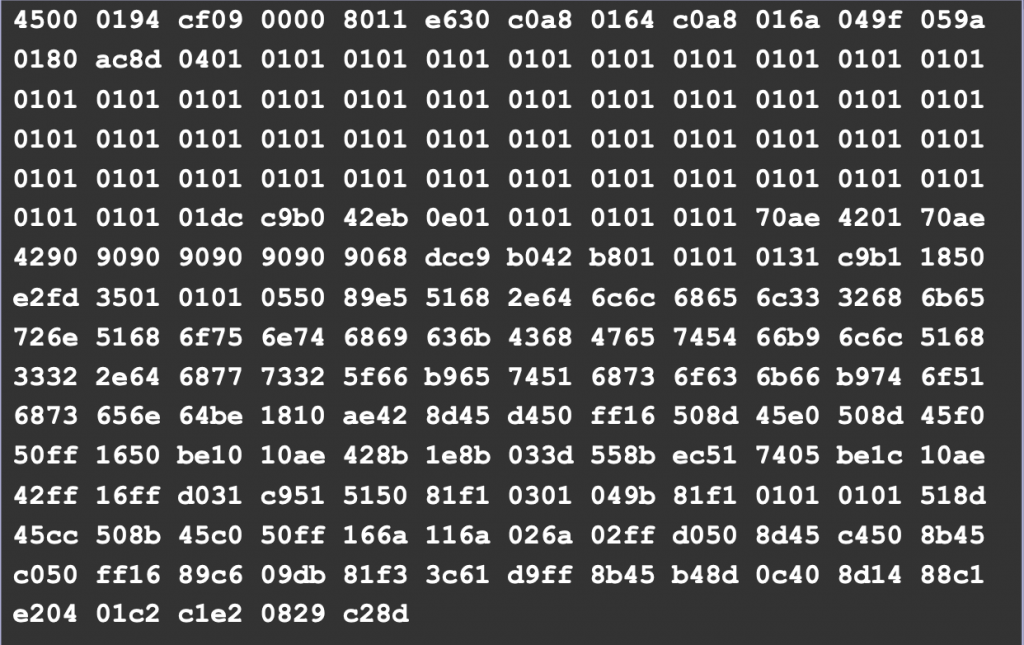
Slammer UDP package (source: SlidePlayer)The 2000s also marked the beginning of malware specifically designed to create botnets, networks of compromised computers used for various malicious activities. Blaster, which also emerged in 2003, exploited a Windows vulnerability (specifically, in a DCOM RPC component) to launch DDoS attacks [18] (see Figure 5), while Sasser, in 2004, targeted another Windows vulnerability (specifically, the LSSASS service in Windows XP and Windows 2000 systems), leading to significant disruption despite not being intentionally destructive [19]. These worms were early examples of malware that sought to leverage a large number of infected systems to conduct coordinated attacks, a trend that would become increasingly prominent. Related to Blaster, it is worth also mentioning the non-malicious Welchia/Nachi worm (classified as a nematode) aimed to remove Blaster infections while patching the vulnerable systems to prevent further infections.
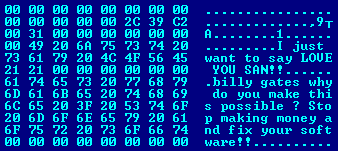
Blaster worm, showing a message left by the programmer to Microsoft founder Bill Gates (source: Wikipedia)Besides Sasser, the year 2004 also saw the emergence of MyDoom, which spread via email and the Kazaa P2P network, launching DDoS attacks and creating backdoors [20]. Santy, the first web worm, targeted phpBB forums, while Witty, the first high-propagation worm, targeted specific security systems [21, 22]. This era also saw the appearance of the first worms targeting non-PC environments. Cabir, which appeared in 2004, was the first worm to infect mobile phones and spread via Bluetooth connections to Symbian-based devices [23]. This marked the beginning of the malware spreading into new environments, paving the way for future attacks on mobile and IoT devices.
In 2005, Zotob spread by exploiting a vulnerability in Windows 2000’s Plug and Play service, turning infected systems into part of botnets [24]. This year was also notable for the Sony BMG rootkit incident. To control the ripping and distribution of music, Sony implemented the XCP rootkit as a way to prevent a user from copying a music CD, while still allowing the CD to play as music [25]. Brontok also emerged this year, spreading via email and removable drives and causing DoS to specific websites such as PlayBoy or Israeli government-related websites [26].
The first macOS-targeting worm, Oompa (or Leap), was released in 2006, spreading via iChat [27]. Inqtana, another macOS worm (technically speaking, classified as a proof-of-concept worm), exploited Bluetooth vulnerabilities [28], while Stration (also known as Warezov), another Windows worm, spread through email and removable drives, forming botnets [29]. Tamiami also appeared this year, and unlike the others, it was a Windows worm incorporating file-infecting behavior.
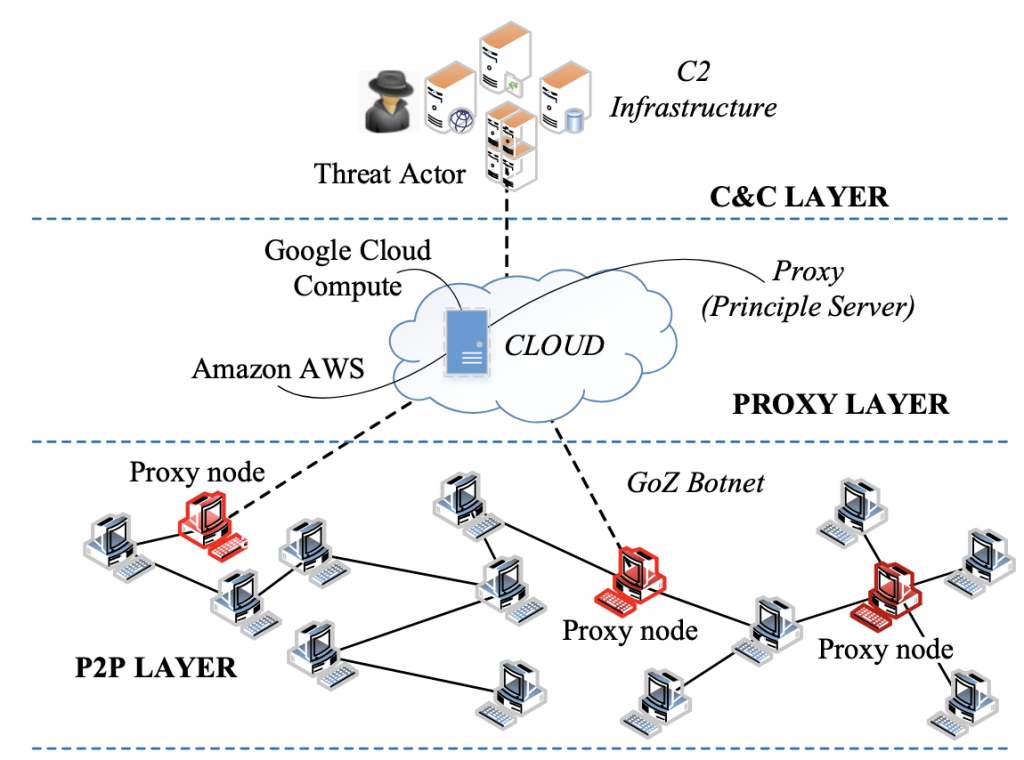
Zhelatin, a mass mailing worm from 2007, utilized a rootkit and keylogger, and infected systems became part of the “Storm Worm” botnet [30]. This year also saw the emergence of Zeus, a sophisticated banking Trojan that stole credentials via web browsers [31, 32] and would later become one of the most long-lived and damaging malware in history, responsible for significant financial losses and featuring prominently in several high-profile takedown operation (see Figure 6 to understand its infrastructure) [33].
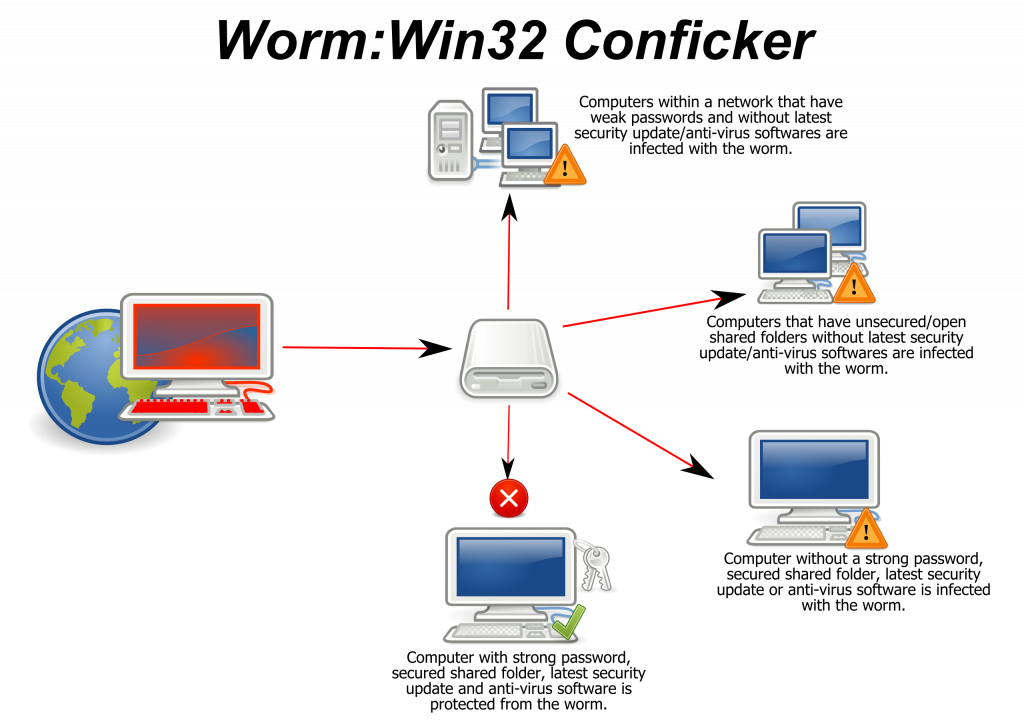
In 2008, social networks experienced their first worm with Koobface, which initially targeted Facebook and later spread to Twitter and MySpace [33]. Conficker (also known as Downadup and Kido), another major worm, exploited the MS08-067 vulnerability, becoming the most widespread infection since Slammer [34]. In particular, exploiting the MS08-067 vulnerability in Windows (this vulnerability would also be exploited two years later by Stuxnet [35]), Conficker demonstrated how modern malware could spread at scale, affecting millions of computers worldwide. It represented a significant escalation in the level of sophistication and coordination seen in malware attacks, using advanced techniques such as domain generation algorithms to evade detection and ensure persistence. The impact of Conflicker was wide, reaching both home users and critical infrastructure, setting a precedent for the scale and severity of future cyber threats. This made a wake-up call for the cybersecurity community, highlighting the urgent need for better vulnerability management and cooperative defense strategies.
And so the turbulent decade of the 2000s comes to an end! This decade saw malware evolve from simple viruses to highly effective self-replicating worms, culminating in Conficker, a worm that highlighted just how serious the threat landscape had become.
References
- The Virus Encyclopedia. Loveletter. [Online; http://virus.wikidot.com/loveletter]. Accessed on February 10, 2023
- Enoch Root. ILOVEYOU: the virus that loved everyone. [Online; https://www.kaspersky.com/blog/cybersecurity-history-iloveyou/45001/], August 2022. Accessed on February 10, 2023.
- Robert S. Mueller. Protecting the U.S. Economy in a Global Age. [Online; https://archives.fbi.gov/archives/news/speeches/protecting-the-u.s.-economy-in-a-global-age], October 2003. Accessed on February 10, 2023.
- Graham Cluley. Memories of the Anna Kournikova worm. [Online; https://grahamcluley.com/memories-anna-kournikova-worm/], February 2011. Accessed on February 10, 2023.
- The Virus Encyclopedia. Sadmind. [Online; http://virus.wikidot.com/sadmind]. Accessed on February 10, 2023
- The Virus Encyclopedia. Codered. [Online; http://virus.wikidot.com/codered]. Accessed on February 10, 2023
- The Malware Wiki. Sadmind. [Online; https://malwiki.org/index.php?title=Sadmind], February 2021. Accessed on February 10, 2023.
- Ryan Permeh and Marc Maiffret. ANALYSIS: .ida “Code Red” Worm. [Online; https://web.archive.org/web/20110722192419/http://www.eeye.com/Resources/Security-Center/Research/Security-Advisories/AL20010717], July 2001. Accessed on February 10, 2023.
- CERT Division. 2001 CERT Advisories. techreport DM17-0052, Carnegie Mellon University, 2017.
- The Malware Wiki. Klez. [Online; https://malwiki.org/index.php?title=Klez], July 2021. Accessed on February 10, 2023.
- The Mental Driller. Metamorphic Permutating High-Obfuscating Reassembler. [Online; http://dsr.segfault.es/stuff/website-mirrors/29A/29a-6/29a-6.602], February 2002. Accessed on February 10, 2023.
- F-Secure. Mylife. [Online; https://www.f-secure.com/v-descs/mylife.shtml]. Accessed on February 10, 2023.
- The Malware Wiki. Tanatos. [Online; https://malwiki.org/index.php?title=Tanatos], February 2021. Accessed on February 10, 2023.
- ANY.RUN. Malware History: Sobig. [Online; https://any.run/cybersecurity-blog/malware-history-sobig/], September 2020. Accessed on February 10, 2023.
- F-Secure. Worm:W32/Slammer. [Online; https://www.f-secure.com/v-descs/mssqlm.shtml]. Accessed on February 10, 2023.
- Stuart Staniford, Vern Paxson, and Nicholas Weaver. How to Own the Internet in Your Spare Time. In Proceedings of the 11th USENIX Security Symposium (USENIX Security 02), 2002
- The Malware Wiki. Spybot. [Online; https://malwiki.org/index.php?title=Spybot], May 2021. Accessed on February 10, 2023.
- The Virus Encyclopedia. Blaster. [Online; http://virus.wikidot.com/blaster]. Accessed on February 10, 2023.
- Duncan Macrae. Everything you need to know about the Sasser worm. [Online; https://techmonitor.ai/technology/cybersecurity/everything-you-need-to-know-about-the-sasser-worm-4213147], April 2014. Accessed on February 10, 2023.
- GetSupport. Mydoom: The Fascinating Story Behind the World’s Fastest Computer Virus. [Online; https://www.getsupport.co.uk/blog/2021-10/mydoom-the-fascinating-story-behind-the-worlds-fastest-computer-virus/], October 2021. Accessed on February 10, 2023.
- F-Secure. Net-Worm:W32/Santy.A. [Online; https://www.f-secure.com/v-descs/santy_a.shtml]. Accessed on February 10, 2023.
- Bruce Schneier. The Witty worm: A new chapter in malware. [Online; https://www.computerworld.com/article/2565119/the-wittyworm–a-new-chapter-in-malware.html], June 2004. Accessed on February 10, 2023.
- F-Secure. Bluetooth-Worm:SymbOS/Cabir. [Online; https://www.f-secure.com/v-descs/cabir.shtml]. Accessed on February 10, 2023.
- The Malware Wiki. Zotob. [Online; https://malwiki.org/index.php?title=Zotob], June 2021. Accessed on February 10, 2023.
- FSFE. Revisiting the Sony Rootkit. [Online; https://fsfe.org/activities/drm/sony-rootkit-fiasco.en.html]. Accessed on February 10, 2023.
- The Malware Wiki. Brontok. [Online; https://malwiki.org/index.php?title=Brontok], June 2021. Accessed on February 10, 2023.
- Rob Griffiths. Leap-A malware: what you need to know. [Online; https://www.macworld.com/article/178862/leapafaq-2.html], February 2006. Accessed on February 10, 2023.
- John Leyden. Mac OS X malware latches onto Bluetooth vulnerability. [Online; https://www.theregister.com/2006/02/17/macosx_bluetooth_worm/], February 2006. Accessed on February 10, 2023.
TODO Checquear si este es de macos o de windows - The Virus Encyclopedia. Stration. [Online; http://virus.wikidot.com/stration]. Accessed on February 10, 2023.
- The Virus Encyclopedia. Zhelatin. [Online; http://virus.wikidot.com/zhelatin]. Accessed on February 10, 2023.
- Malwarebytes Labs. The life and death of the ZeuS Trojan. [Online; https://www.malwarebytes.com/blog/news/2021/07/the-life-anddeath-
of-the-zeus-trojan], July 2021. Accessed on February 10, 2023. - Konstantinos P. Grammatikakis, Ioannis Koufos, Nicholas Kolokotronis, Costas Vassilakis, and Stavros Shiaeles. Understanding and Mitigating Banking Trojans: From Zeus to Emotet. In 2021 IEEE International Conference on Cyber Security and Resilience (CSR), pages 121–128, 2021.
- FBI. GameOver Zeus Botnet Disrupted. [Online; https://www.fbi.gov/news/stories/gameover-zeus-botnet-disrupted]. Accessed on November 2, 2024.
- The Malware Wiki. Koobface. [Online; https://malwiki.org/index.php?title=Koobface], April 2021. Accessed on February 10, 2023.
- AVG South Africa. Conficker/Downadup/Kido worm infects over 9 Million PCs. [Online; https://www.itweb.co.za/content/JN1gP7O2BA5vjL6m], March 2009. Accessed on February 10, 2023.
- Ralph Langner. Stuxnet: Dissecting a Cyberwarfare Weapon. IEEE Security & Privacy, vol. 9, no. 3, pp. 49–51
And that’s it, folks! In this blog post, we’ve explored the adolescence of malware in the 2000s, a period marked by a shift towards self-replicating worms that exploited vulnerabilities in widely used software (especially, web servers), combining sophisticated propagation techniques, and causing significant economic damage. This era laid the frundwork for modern malware, emphasizing the growing importance of Internet security and the constant challenges in defending against rapidly evolving digital threats. In the next blog post, we’ll dive into malware’s adulthood starting in 2010, where sophisticated, targeted attacks, including ransomware and APTs, reshaped the threat landscape again. See you in the next blog post!
