TL;DR: Ransomware encrypts victims’ files with keys that must exist in memory at runtime. If defenders can access those keys while the malware is still running, they could decrypt files without paying a ransom. We introduce KeyReaper: a live memory analysis tool designed to extract cryptographic keys from running Windows processes in real time. By targeting heap memory and using key-specific heuristics, KeyReaper enables fast and reliable key recovery, even in real-world ransomware cases like WannaCry or Avaddon. If you’re curious to learn more, visit our poster session at DIMVA 2025 this week or read the full paper here (or here) or our poster here.
Ransomware’s Achilles’ Heel: Runtime Keys in Memory
Ransomware continues to dominate the cyberthreat landscape, attacking availability by encrypting files and holding them hostage. While attackers often employ strong cryptographic algorithms, those keys must be generated and stored in memory during execution. This brief moment offers a unique opportunity for defenders.
Traditionally, forensic analysts have relied on static, often post-mortem, memory dumps, which limits their effectiveness. But what if we could pause ransomware during execution, inspect its memory in real time, and extract the encryption keys directly? That’s the core idea of KeyReaper.
Meet KeyReaper
KeyReaper is an open-source tool specifically designed to locate cryptographic keys in active Windows processes using live memory analysis. It does not detect ransomware, but is designed to be deployed after an antivirus or EDR solution detects a process.
The tool focuses on heap memory, where dynamic key material is typically stored during encryption operations. By limiting the scope, KeyReaper improves performance and accuracy while minimizing false positives.
KeyReaper is structured around three main modules, as depicted in Figure 1:
- Process Capture: Pauses the ransomware process to stabilize memory.
- Heap Extraction: Isolates and copies heap segments from the paused process.
- Key Scanning: Applies pluggable detection algorithms to locate key structures in memory.
These modules are orchestrated using a command-line interface ideal for integration into automated incident response workflows.
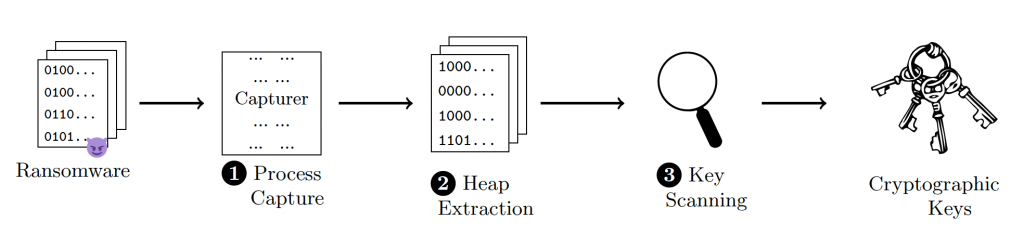
KeyReaper.How It Works
The key scanning phase leverages multiple analysis modules:
- AES Round Key Reconstruction: Reconstructs AES keys using derived round key patterns, even if the original key is not stored directly.
- CryptoAPI Key Scanner: Detects keys managed using Microsoft’s CryptoAPI, commonly used by malware such as Avaddon and WannaCry.
These modules rely on techniques such as DLL injection, pattern matching, and heap structure analysis, using APIs such as NtSuspendProcess and ReadProcessMemory. The heavy lifting is handled in C++, ensuring low overhead and fast execution.
Evaluation Highlights
We rigorously tested KeyReaper in four dimensions:
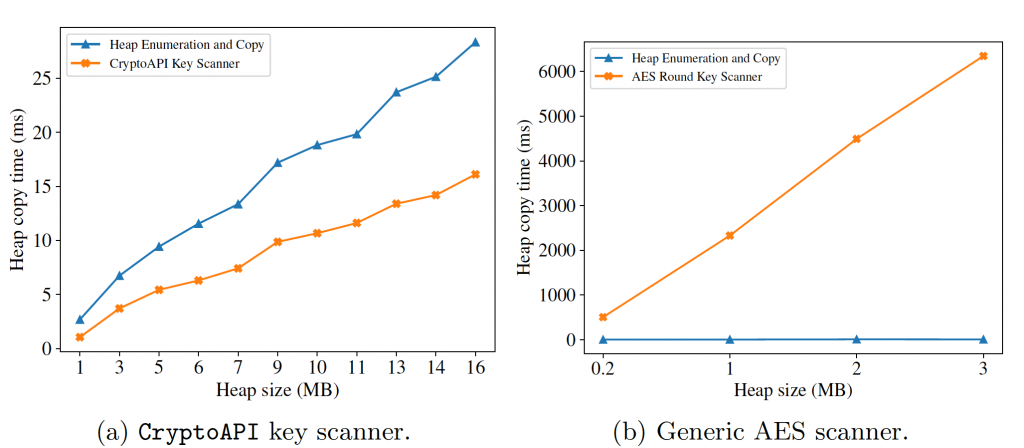
- Reaction Time: Efficient heap copying and scanning, with the CryptoAPI scanner significantly outperforming the generic AES module.
- False Positives: Zero false detections on noisy synthetic heaps and innocuous software such as Audacity or Notepad++.
- Key Accuracy: Keys extracted by
KeyReaperexactly matched those exported using legitimate CryptoAPI functions in over 1,000 test runs. - Real Ransomware:
KeyReapersuccessfully extracted usable keys from Avaddon and WannaCry, enabling decryption of test files by comparing their SHA256 hashes after decryption.
Figure 2 show the time-to-memory ratio of each scanning module and confirm the tool’s reliability in real-world situations.
Why this matters?
KeyReaper offers defenders a practical, real-time method to recover encryption keys before irreversible damage is achieved. It improves ransomware mitigation by enabling:
- Live key recovery for decryption, avoiding ransom demands.
- Malware reverse engineering by separating malicious logic from built-in cryptographic operations.
- Compliance testing by validating how the software handles key material in memory.
It bridges the gap between detection and remediation, helping SOCs and analysts respond more quickly and effectively.
What’s next?
We are actively developing new features, including:
- Support for additional cryptographic libraries such as OpenSSL and Crypto++.
- Detection of more algorithms, such as Salsa20.
- Case dump analysis for offline forensics.
- Support for new heap types, such as the Windows segmented heap.
- Integration with audit and compliance workflows using legitimate encryption tools.
We are also planning to explore heap evasion and obfuscation techniques used by ransomware authors to stay ahead as defenders.
Funding Acknowledgments
This research was supported in part by grant PID2023-151467OA-I00 (CRAPER), funded by MICIU/AEI/10.13039/501100011033 and by ERDF/EU, by grant TED2021-131115A-I00 (MIMFA), funded by MICIU/AEI/10.13039/501100011033 and by the European Union NextGenerationEU/PRTR, and the University of Zaragoza, by grant Proyecto Estratégico Ciberseguridad EINA UNIZAR, funded by the Spanish National Cybersecurity Institute (INCIBE) and the European Union NextGenerationEU/PRTR, and by grant Programa de Proyectos Estratégicos de Grupos de Investigación (T21-23R), funded by the University, Industry and Innovation Department of the Aragonese Government.

And that’s all, folks! In this post, we introduce KeyReaper, our tool for live cryptographic key extraction from active Windows processes: a practical advancement in ransomware mitigation and digital forensics investigation. If you’re attending DIMVA 2025, please visit our poster session and let’s chat! We’d love to hear your thoughts, answer your questions, and explore collaboration ideas. In the meantime, feel free to dig deeper into our paper, contact us, or contribute to the project as we continue to improve our static and dynamic malware analysis tools. Thanks for reading, and stay secure!
Declaration of Generative AI Technologies in the Writing Process
During the preparation of this post, the author used ChatGPT (GPT4-o model) to improve readability and language. After using this tool, the author reviewed and edited the content as necessary and takes full responsibility for the content of this publication.
