TL;DR: While macOS was once considered a haven of security, it’s now an increasingly popular target for sophisticated malware. Our recent large-scale study of over 57,000 macOS malware samples reveals how attackers are using the MITRE ATT&CK framework to bypass security, maintain persistence, and evade detection through techniques such as scripting, hidden files, and virtual environment detection. Interested? Keep reading this briefing or get the full paper here.
Why macOS Is No Longer the “Safe” Option
For years, the macOS platform enjoyed a reputation for being relatively secure compared to its peers. However, as the adoption of Apple devices has skyrocketed in both personal and corporate environments, so has the interest of malicious actors. Recent data highlights a significant upward trend in the volume and sophistication of attacks specifically targeting macOS.
Threat Analysis: The Study
To understand how these modern threats operate, we have conducted a comprehensive analysis of 57,636 macOS malware samples collected between 2006 and 2024. Through static analysis (inspecting file structures) and dynamic analysis (observing execution in isolated environments), we provide a detailed view of the current threat landscape.
Key Findings: Tactics and Techniques
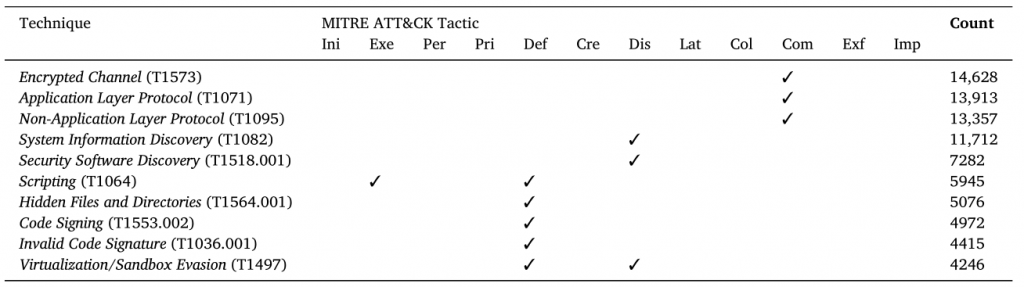
We aligned our findings with the MITRE ATT&CK framework to categorize adversary behavior. Here’s how malware is currently affecting Apple (Figure 1 shows the top 10 most frequently used TTPs in our dataset):
- Defense Evasion (76.65% of samples): This is the most common tactic. Malware authors prioritize concealment using techniques such as
- Scripting (T1064): Executing malicious code directly in the macOS shell to avoid detection.
- Hidden Files (T1564.001): Prefixing filenames with a period (‘.’) to make them invisible in the Finder.
- Virtualization Evasion (T1497): Detecting whether the malware is running in a sandbox or virtual machine and modifying its behavior to avoid analysis.
- Persistence (26.32% of samples): To ensure survival after system restarts, attackers often abuse:
- Launch Agents (T1543.001): Creating specific .plist files to ensure the malware runs every time a user logs in.
- Dynamic library addition (T1546.006): Malicious code injection during the system boot process.
- Discovery (83.90% of samples): Once inside, the malware focuses on gathering detailed information about the target’s operating system and hardware.
The role of programming languages
The study also revealed that Objective-C remains a dominant language for macOS malware due to its deep integration with Apple’s APIs. While Swift is becoming the standard for harmless software, its presence in the malware landscape is still minimal, but growing.
Takeaways for defenders
Understanding these patterns is the first step toward better protection. The heavy reliance on defense evasion suggests that signature-based tools alone are no longer sufficient. Security professionals should:
- Monitor launch agents and daemons for unauthorized persistence.
- Improve sandbox detection to counter evasion techniques.
- Audit shell scripts and command-line activity to detect suspicious patterns.
For more details (and explore the full set of tables and graphs with results), see our full work published in Computers & Security.
Funding Acknowledgments
This research was supported in part by grant PID2023-151467OA-I00 (CRAPER), funded by MICIU/AEI/10.13039/501100011033 and by ERDF/EU, by grant TED2021-131115A-I00 (MIMFA), funded by MICIU/AEI/10.13039/501100011033 and by the European Union NextGenerationEU/PRTR, and the University of Zaragoza, by grant Proyecto Estratégico Ciberseguridad EINA UNIZAR, funded by the Spanish National Cybersecurity Institute (INCIBE) and the European Union NextGenerationEU/PRTR, and by grant Programa de Proyectos Estratégicos de Grupos de Investigación (refs. T21-23R), funded by the University, Industry and Innovation Department of the Aragonese Government.

And that’s all, folks! Stay tuned for our next deep dive into the evolution of macOS security. In the meantime, we encourage you to read the full article in the COSE journal, explore the dataset details, or reach out to us if you’re interested in collaborating on further macOS threat research. Thanks for reading, and stay secure!
Declaration of Generative AI Technologies in the Writing Process
During the preparation of this post, the author used Gemini (Gemini 3 model) to improve readability and language. After using this tool, the author reviewed and edited the content as necessary and takes full responsibility for the content of this publication.
