TL;DR: This is the third part of a series of monthly blog posts that we will be dedicated to explaining the evolution of malware over the years. In this post, we will describe the puberty of malware, counting the malicious programs that appeared in the 1990s, which were mainly viruses. The early infancy of malware, describing the self-replicating predatory programs that appeared in the 1970s, is described in Part 1. Likewise, the childhood of malware, describing the first proofs of concept of malicious behaviors that appeared in the 1980s, is described in Part 2.
The Puberty of Malware: The Rise of Viruses. The 90s
Until this decade, most malware had not been conceived for malicious purposes, being simple proofs of concept. From the 1990s onwards, this phenomenon began to change and numerous malicious programs with potentially harmful behavior began to appear.
Inspired by Vienna, a malware from the late 1980s that infected executable files (specifically .COM files), Mark Washburn developed the Chameleon virus in 1990. Targeting the MS-DOS system, this malware is also a .COM infector. Chameleon is considered to be the first polymorphic virus. This type of virus is a complex file infector that can create modified versions of itself in an attempt to evade detection, but follows the same basic routines after each infection.
The Michelangelo boot sector virus was first discovered in February 1991. Targeting MS-DOS systems, it incorporated a logic bomb to activate annually on March 6 (the birthday of the Renaissance artist Michelangelo). When activated, it overwrote parts of the hard disk with random data, making all information inaccessible. Despite receiving a lot of media attention, claiming that the number of systems wiped would be in the millions [1], the actual impact of this virus was very small [2]. This media hype was relevant to anti-virus software companies, which got a boost in sales due to people’s hysteria. Figure 1 shows Michelangelo‘s dropper, used to infect floppy drives and thus spread the virus.
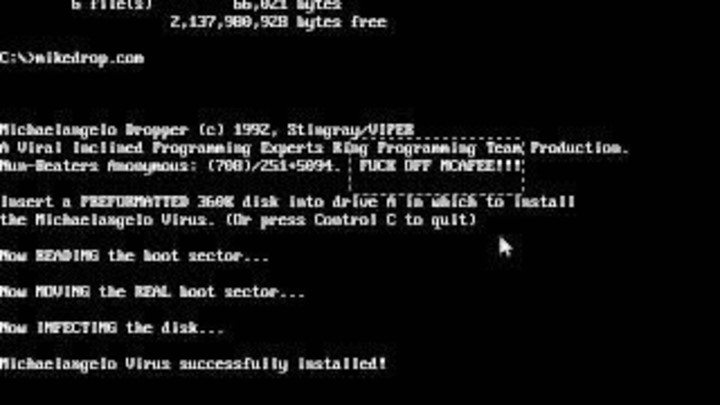
Michelangelo boot sector virus (source: Clarín)Later, in 1994 the Onehalf multipartite virus appeared. A multipartite virus is a virus that simultaneously infects a device’s boot sector and executable files. This virus was very destructive, as each time an infected system was booted, it encrypted the last two unencrypted sectors of the hard drive. Eventually, the hard drive became fully encrypted if the malware was not removed in time.
A year later, the first Word macro virus found “in the wild”, dubbed Concept, was discovered. A macro virus is a computer virus written in the same macro language used to create software programs with Microsoft Excel or Word, among others. The first true macro virus is considered to be DMV, although it was developed as a proof of concept just to keep users informed about what can be done using macros [3]. Specifically, Concept targeted Microsoft Word 95 and 6.0 software versions. Figure 2 shows two different versions of this macro virus.
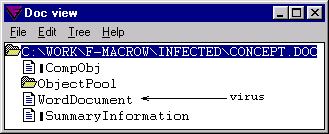
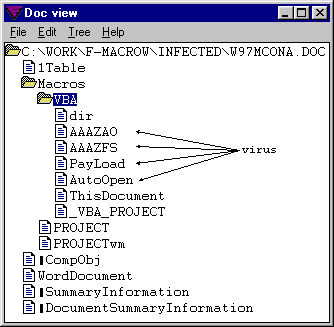
Concept Word macro virus (source: Vesselin Bontchev, FRISK Software International)The year 1996 brought us numerous viruses that were the first of their kind. Developed by the VLAD group, Bizatch is considered to be the first virus specifically targeting Windows 95. Each time it runs, up to three executable files are infected. Likewise, Laroux was the first macro virus to target Microsoft Excel. Unlike Concept, Laroux only runs on Windows. The VLAD group also released Staog, considered to be the first virus for Linux. Using three known vulnerabilities, it was able to gain privileges and install itself in kernel memory, and then began infecting executable files when run, regardless of their owner or privilege level.
In mid-1998, the infamous Chernobyl (also known as CIH after the initials of the name of its alleged creator, Chen Ing Hau) was discovered. The infection process of this file infector virus was unique at the time, as the size of the infected files never increased: it searched for empty, unused spaces in executable files and then split itself into chunks, inserting them into the unused spaces. Chernobyl targeted Windows 95 and Windows 98 operating systems and spread very quickly, as it was distributed through pirated software [4]. In addition to the file infection, Chernobyl incorporated a logic bomb that activated on April 26, executing two payloads aimed at destroying hard drive data and corrupting the computer’s Flash BIOS, causing permanent damage. Figure 3 shows a binary dump of a Chernobyl sample, where reference to the initials of its supposed creator and the software version appear.
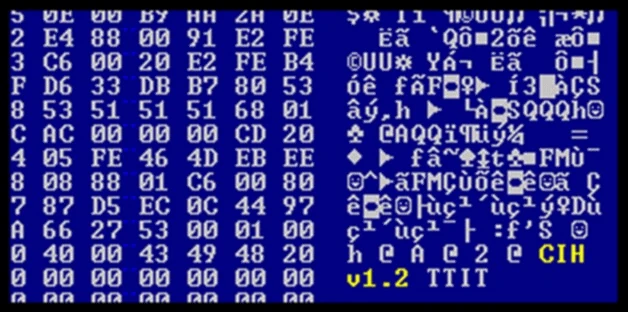
Chernobyl file infector virus (source: Wiki Malware)This decade ended with Melissa, a Word macro worm-capable virus that appeared in March 1999. This malware targeted Microsoft Word, and if the infected computer had Microsoft Outlook 97 or Outlook 98 installed, it was able to replicate and send itself to the first fifty email contacts read from the Outlook Address Book [5]. Figure 4 shows an example of the email sent by Melissa. Major companies such as Microsoft, Intel, or the US Marine Corps [6] were affected by this malware. This 1:50 infection ratio caused significant network traffic that slowed down their email systems, causing a denial of service on the systems. Like Michelangelo, it received a lot of media attention and although it spread, the actual impact was very small.
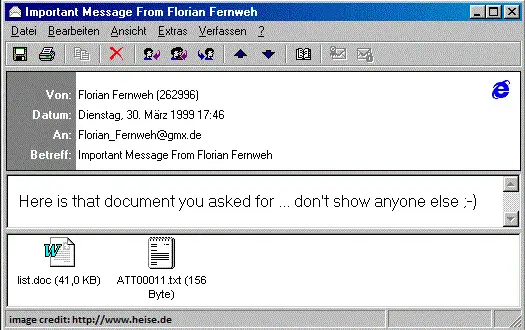
Melissa Word macro worm-capable virus (source: CyberHoot)References
- Christine González. Paint It Scary : Businesses, Others Scramble to Thwart Michelangelo PC Virus . [Online; https://www.latimes.com/archives/la-xpm-1992-03-04-fi-3207-story.html], March 1992. Accessed on Februrary 10, 2023.
- Michael W. Miller. ‘Michelangelo’ Scare Ends In an Anticlimax. The Wall Street Journal, March 1992.
- F-Secure. Dmv. [Online; https://www.f-secure.com/v-descs/dmv.shtml]. Accessed on February 10, 2023.
- F-Secure. Virus:DOS/CIH. [Online; https://www.f-secure.com/v-descs/cih.shtml]. Accessed on February 10, 2023.
- FBI. Melissa Virus. [Online; https://www.fbi.gov/history/famous-cases/melissa-virus]. Accessed on February 10, 2023.
- Paul McNamara. Melissa virus turning 15 … (age of the stripper still unknown). [Online; https://www.networkworld.com/article/2226599/melissa-virus-turning-15—-age-of-the-stripper-still-unknown-.html], March 2014. Accessed on February 10, 2023.
And that’s it, folks! In this blog post we have summarized the puberty of malware in the 1990s, when viruses began to dominate the malware ecosystem. In the next blog post, we’ll summarize the adolescense of malware in the 2000s, when the malware landscape shifted primarly to worms. See you in the next blog post!
