TL;DR: This is the second part of a series of monthly blog posts that we will be dedicated to explaining the evolution of malware over the years. In this post, we will describe the childhood of malware, counting the malicious programs that appeared in the 1980s, which were mainly the first proofs of concept of malicious behaviors. The early infancy of malware, describing the self-replicating predatory programs that appeared in the 1970s, is described in Part 1.
The Childhood of Malware: Proofs of concept. The 80s
Later, in 1984, and inspired by the behavior of biological viruses, Fred Cohen defined the term (computer) virus in his doctoral thesis as “a program that can infect other programs by modifying them to include a, possibly evolved, version of itself” [1]. This is the first known reference to malicious behavior in software.
One of the first self-replicating software to spread “in the wild” was Elk Cloner in 1982. Developed by Richard Skrenta at the age of 15, this malware targeted the Apple DOS 3.3 operating system. In particular, Elk Cloner is classified as a boot sector virus, a type of virus that infects the boot sectors of floppy disks or hard disks to spread. When the computer boots from an infected floppy disk, the malware copies itself into computer’s memory and infects the system. Then, when an uninfected disk is inserted into the infected system, the malware copies itself onto the disk, allowing it to spread from one disk to another. Regarding malicious behavior, Elk Cloner incorporated 14 different manifestation behaviors, ranging from obvious behavior (displaying a poem on the computer screen) to error-like and evasive behaviors [2]. Figure 1 shows the message that this program displayed when the system was infected.
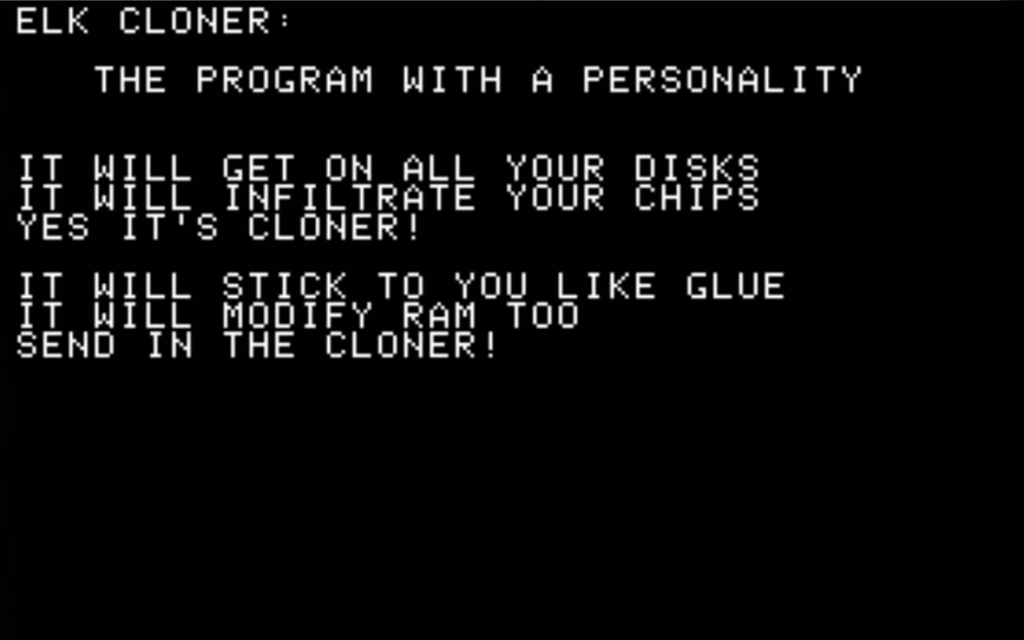
Elk Cloner program (source: Wikipedia)Later on, in 1984, Ken Thompson introduced the first known “Trojan horse“. A Trojan horse is a type of malware that disguises itself as a legitimate program, misleading users about its true intent. During his Turing Award lecture [3], he presented how a C compiler could be abused to change the behavior of certain programs such as the UNIX login program during compilation (in particular, it would allow the attacker to log into the system as any user).
The first known virus targeting IBM/PC systems was discovered in 1986. Developed by the Alvi brothers from Pakistan, Amjad Farooq and Basit Farooq, Brain is also classified as a boot sector virus. In particular, it replaced the boot sector of a floppy disk with a copy of the virus, copying the actual boot sector to another sector that was marked as a bad sector (see Figure 2 below to see what a Brain-infected boot sector looked like). This virus inspired John McAfee to create what is considered to be the first antivirus program, VirusScan, an anti-virus program specifically aimed at removing the Brain virus [4].
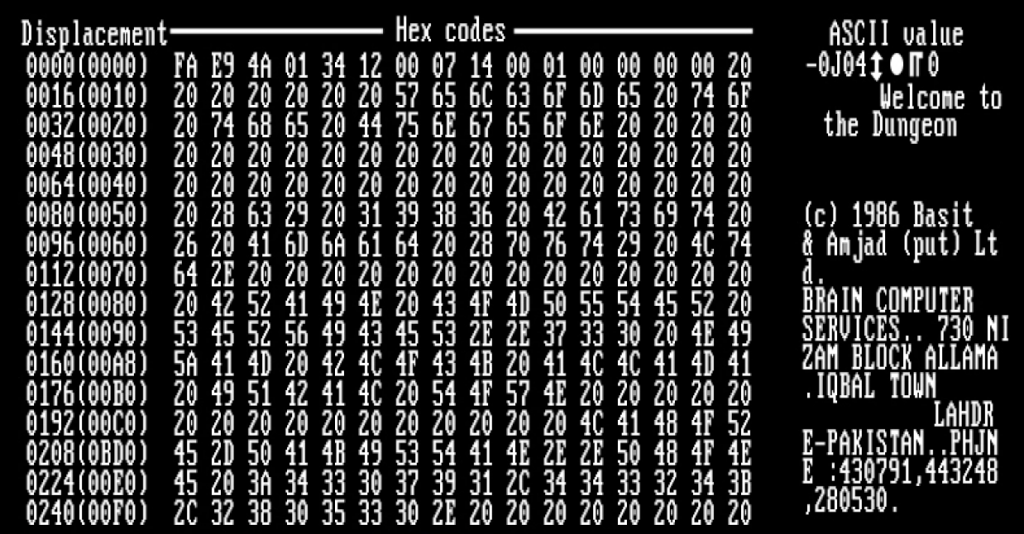
Brain virus (source: Wikipedia)During 1987, the first virus directed at MS-DOS systems appears. Dubbed Jerusalem, it deleted any program the user tried to run and infected every executable file running in the MS-DOS system. By this kind of behavior, Jerusalem is denominated as a file virus. Unlike other viruses at the time, this malware is also a logic bomb, as the original variant was activated on Friday the 13th in every year except 1987 [5]. Later variants of Jerusalem changed the activation day and the malicious behavior [6]. During the same year, the number of boot sector virus ramped up as well. Well-known examples are Ping-pong, which displayed a small ball bouncing around the screen when it became active [7], and Stoned, which sometimes (with a one in eight chance) displayed the message “Your PC is now Stoned!” when the infected computer started [8].
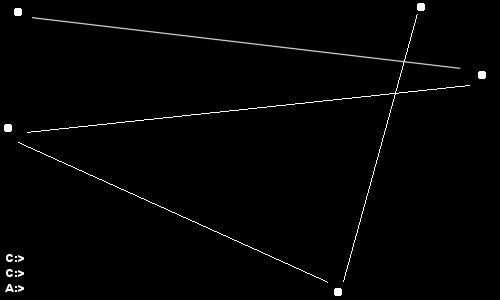
Ping-pong boot sector virus (source: Wikipedia)In 1988, Robert T. Morris released what is considered to be the first worm malware, the Morris worm [9]. Unlike viruses, computer worms replicate themselves to spread to other computers over computer networks. Morris targeted DEC VAX/Sun3 systems running BSD and exploited security flaws in the fingerd and sendmail programs to gain privileges on the infected system and spread, respectively. In fact, this malware is known as the first real exploitation of an out-of-bounds vulnerability (caused by a gets function in the fingerd program) to obtain a remote shell on infected systems.
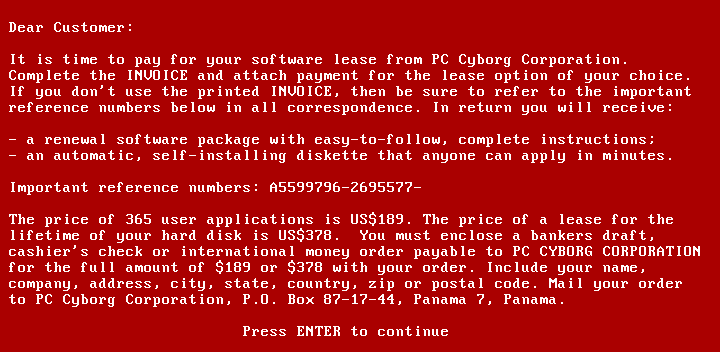
AIDS Trojan Horse (source: Wikipedia)Finally, in 1989, Joseph L. Popp developed AIDS Trojan Horse. The name is misleading as it is not a Trojan but is considered the first ransomware, a type of malware that threatens to publish the victim’s personal data or permanently block access to computer files unless a ransom be paid. In particular, AIDS hid the directories and encrypted (using symmetric cryptography) or locked file names to block access to the infected system [10].
References
- Fred Cohen. Computer viruses: Theory and experiments. Computers & Security, 6(1):22–35, 1987.
- Scott Levy and Jedidiah R. Crandall. The Program with a Personality: Analysis of Elk Cloner, the First Personal Computer Virus. CoRR, abs/2007.15759, 2020.
- Ken Thompson. Reflections on Trusting Trust. Commun. ACM, 27(8):761–763, aug 1984.
- Steve Morgan. John McAfee: Sex, Lies and VirusScan. [Online; https://cybersecurityventures.com/john-mcafee-sexlies-and-virusscan/], February 2019. Accessed on February 10, 2023.
- F-Secure. Jerusalem. [Online; https://www.f-secure.com/v-descs/jerusale.shtml]. Accessed on Feburary 10, 2023.
- Patricia Hoffman. Jerusalem Virus. [Online; https://wiw.org/~meta/vsum/view.php?vir=698], 1998. Accessed on February 10, 2023.
- F-Secure. Ping-Pong. [Online; https://www.f-secure.com/v-descs/pingpong.shtml]. Accessed on February 10, 2023.
- Peter Kleissner. Stoned Bootkit, 2009. BlackHat USA 2009.
- Eugene H. Spafford. The Internet Worm Program: An Analysis. techreport CSD-TR-823, Purdue University, December 1988.
- Jim Bates. Trojan Horse: AIDS Information Introductory Diskette Version 2.0. Virus Bulletin, pages 3–6, January 1990.
And that’s all, folks! In this blog post we have summarized the childhood of malware in the 1980s, when primarily proof-of-concepts of malicious behavior populated the malware ecosystem. In the next blog post, we will recap the puberty of malware in the 1990s, when many viruses began to proliferate. See you in the next blog post!
