TL;DR: This is the first part of a series of monthly blog posts that we are going to dedicate to explaining the evolution of malware over the years. In this post, we will describe the early infancy of malware, counting the self-replicating predatory programs that appeared in the 1970s.
Introduction
Almost 50 years have passed since the first software developed with “malicious” intentions, the Creeper program, came to light. [Note that we have intentionally put the term malicious in double quotes, as this program was not actively causing data corruption, because its purpose was to send a certain string to the teletype.] Initially developed as a proof of concept by Bob Thomas at BBN in 1971, this program is generally accepted as the first computer worm as it was capable of copying itself and moving between DEC PDP-10 mainframes running TENEX OS [1].
Since then, the nefarious — and really malicious — purposes of malicious software (malware) have spread, giving rise to different types of malware depending on their main behavior, such as ransomware, bankers, or simply viruses, to name a few. The purposes have shifted, from the interest in gaining kudos from the community to simply causing harm and to earning income. In addition, we have gone from counting annual malware in the tens to thousands and millions.
But, how has this evolution been during these years? In these blog posts, we review the history of malware, describing the evolution of malware from proof of concept to cybercrime. Join us on this exciting trip into malware history!
The Infancy of Malware: Self-Replicating Programs. The 70s
The first reference in the literature to a program with predatory self-replicating behavior was given by John von Neumann in various talks during 1948 and 1949, where he presented various parts of his theory of self-reproducing automata [2]. This idea was further developed in 1959, when Bell Computer Labs created CoreWar, a computer game based on this von Neumann theory. In this game, the programs fight each other with the aim of occupying all the memory, thus eliminating the other opponents.
This concept of self-replicating programs continued to be of interest to the hacker (we take the second definition of hacker as in [3]: “a person who uses or writes computer programs with enthusiasm and skill”) community through the 1970s. In 1971, Bob Thomas Morris at BBN Technologies developed Creeper, a DEC PDP-10 assembly program that moved between TENEX systems over the ARPANET [4, 5]. This proof-of-concept program is considered as the first computer worm. A worm is a type of malware that spreads itself often using computer networks to other computers. In any event, Creeper is not considered malware since it did not cause damage to data or systems (it simply typed the message “I’M THE CREEPER : CATCH ME IF YOU CAN!” on the Model 33 ASR teletype; see Figure 1 below). Shortly after, Ray Tomlinson (also working at BBN Technologies) created a self-replicating program dubbed Reaper, which is considered to be the first anti-virus software, dedicated to move through the ARPANET removing copies of Creeper.
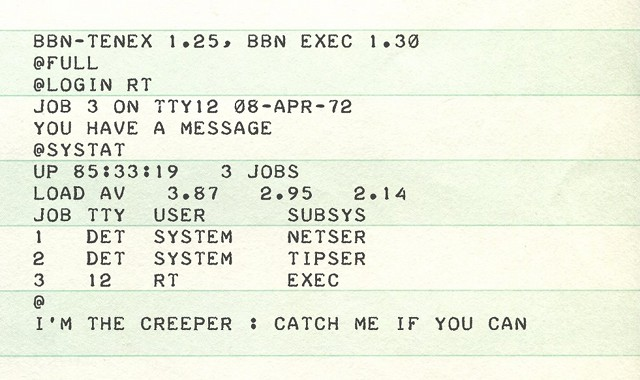
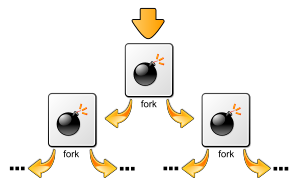
Creeper program (source: [4])In 1974, another self-replicating program targeting IBM System/360 mainframes dubbed Wabbit was developed. Although the true origin of this term is unknown, it is presumed that it comes from the mythical phrases of the animated character Elmer Fudd. Unlike Creeper, Wabbit is considered a program with malicious intent, as it replicates itself on the infected system (simply continuously forking the process) until the system crashed due to resource exhaustion, causing thus a denial of service (DoS) in the system. This type of DoS attack is also known as a fork bomb (see Figure 2).
In the same year, John Walker developed ANIMAL, a computer game for the UNIVAC 1108 computers running the Exec-8 operating system. In essence, the game tried to guess which animal the user is thinking of with a set of questions. The game became very popular and other UNIVAC users began to ask the author to send them a copy of the game, which was not so easy as the program had to be recorded on magnetic tape and sent by mail. To make things easier, in 1975 Walker created PERVADE, a subroutine code added to ANIMAL that allowed it to replicate itself in the system. Because of this, ANIMAL (with the PERVADE routine) is considered to be the first computer Trojan horse. This term is used to define any malware that misleads users about its true intent. Like Creeper, this software is not considered to have malicious intent.
References
- Peter Szor. Fighting Computer Virus Attacks. In 13th USENIX Security Symposium (USENIX Security 04), San Diego, CA, August 2004. USENIX Association.
- John von Neumann. Theory of Self-Reproducing Automata. Technical report, University of Illinois Press, 1966.
- Oxford University Press. Definition of hacker noun from the Oxford Advanced Learner’s Dictionary. [Online; https://www.oxfordlearnersdictionaries.com/definition/english/hacker], 2023.
- Core War: Creeper & Reaper. [Online; https://corewar.co.uk/creeper.htm].
- David Ferbrache. Historical Perspectives, pages 5–30. Springer London, London, 1992.
- John Walker. PERVADE Source Code. [Online; https://www.fourmilab.ch/documents/univac/pervade.html], August 1996.
And that’s all, folks! In this blog post we have summarized the early infancy of malware in the 1970s, when primarily self-replicating programs populated the malware ecosystem. In the next blog post, we will recap the malware’s childhood back in the 1980s, when a lot of proof-of-concept started appearing. See you in the next blog post!

2 Pingbacks